Exhibit
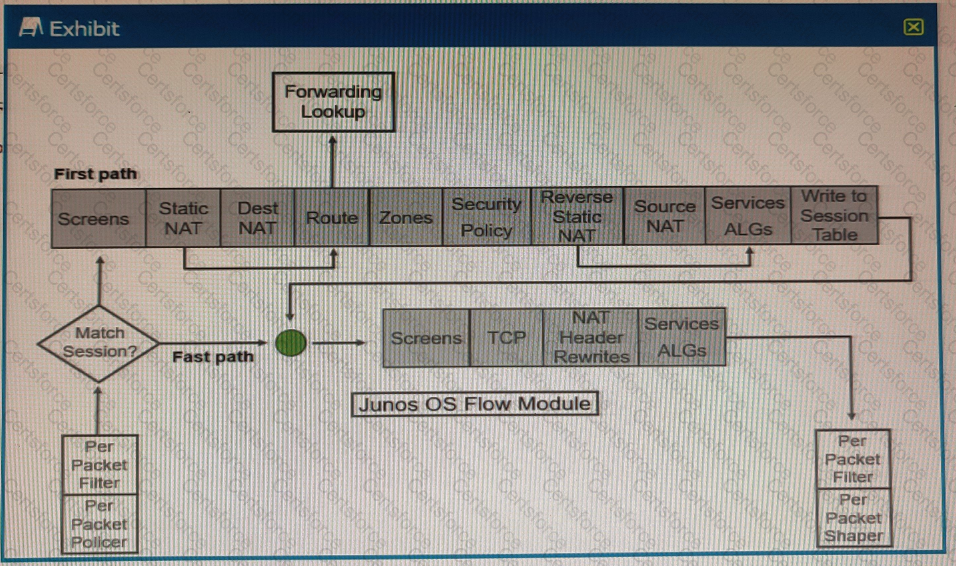
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Which two statements are true about the vSRX? (Choose two.)
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
Which two statements about unified security policies are correct? (Choose two.)
Which two statements are correct when considering IPS rule base evaluation? (Choose two.)
Which statement regarding Juniper Identity Management Service (JIMS) domain PC probes is true?
Which two features are configurable on Juniper Secure Analytics (JSA) to ensure that alerts are triggered when matching certain criteria? (Choose two.)
You are troubleshooting unexpected issues on your JIMS server due to out of order event log timestamps.
Which action should you take to solve this issue?
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
What are two benefits of using a vSRX in a software-defined network? (Choose two.)