How are logical networks assigned to endpoints?
Where do you look to determine when and why the FortiNAC made an automated network access change?
Which connecting endpoints are evaluated against all enabled device profiling rules?
By default, if after a successful Layer 2 poll, more than 20 endpoints are seen connected on a single switch port simultaneously, what happens to the port?
Refer to the exhibit, and then answer the question below.
Which host is rogue?
An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
How does FortiGate update FortiNAC about VPN session information?
View the output.
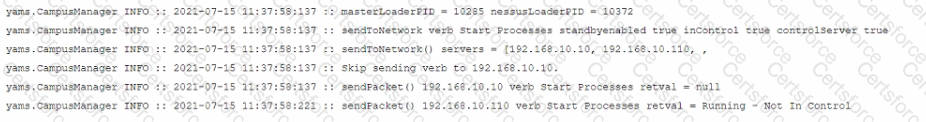
Examine the communication between a primary FortiNAC (192.168.10.10) and a secondary FortiNAC (192.166.10.110) configured as an HA pair What is the current state of the FortiNAC HA pair?
In an isolation VLAN which three services does FortiNAC supply? (Choose three.)
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?