Exhibit.
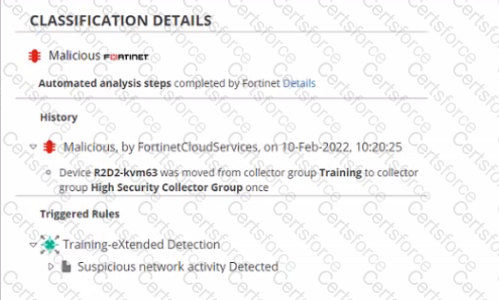
Based on the event shown in the exhibit which two statements about the event are true? (Choose two.)
Refer to the exhibit.
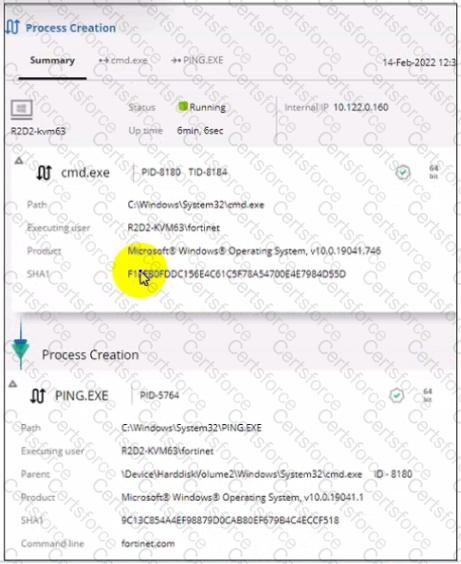
Based on the threat hunting event details shown in the exhibit, which two statements about the event are true? (Choose two.)
Refer to the exhibit.
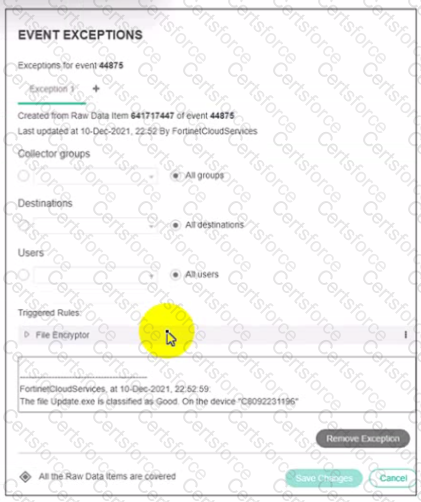
Based on the event exception shown in the exhibit which two statements about the exception are true? (Choose two)
What is the role of a collector in the communication control policy?
An administrator finds a third party free software on a user's computer mat does not appear in me application list in the communication control console
Which two statements are true about this situation? (Choose two)
What is the benefit of using file hash along with the file name in a threat hunting repository search?
Refer to the exhibits.
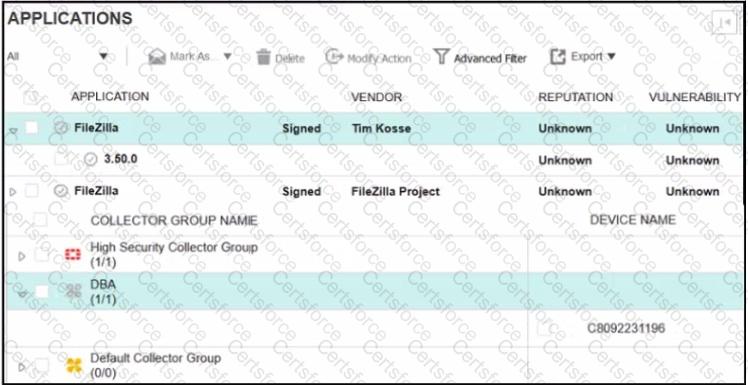

The exhibits show application policy logs and application details Collector C8092231196 is a member of the Finance group
What must an administrator do to block the FileZilia application?
Which security policy has all of its rules disabled by default?
Refer to the exhibit.
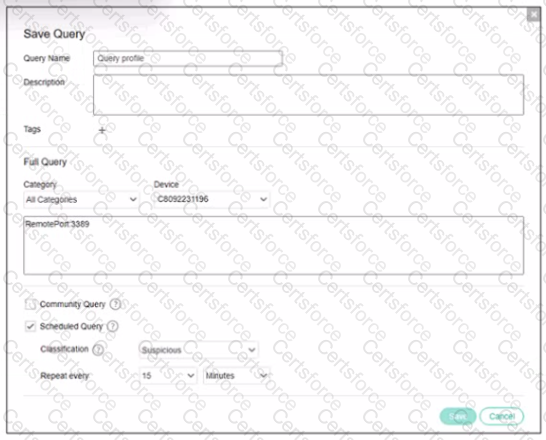
Based on the threat hunting query shown in the exhibit which of the following is true?