Refer to the exhibit.
In your Amazon Web Services (AWS), you must allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet. However, your HTTPS connection to the FortiGate VM in the Customer VPC is not successful.
Also, you must ensure that the Customer VPC FortiGate VM sends all the outbound Internet traffic through the Security VPC.
How do you correct this issue with minimal configuration changes? (Choose three.)
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
Refer to the exhibit.

A managed security service provider (MSSP) administration team is trying to deploy a new HA cluster in Azure to filter traffic to and from a client that is also using Azure. However, every deployment attempt fails, and only some of the resources are deployed successfully. While troubleshooting this issue, the team runs the command shown in the exhibit.
What are the implications of the output of the command?
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?
Refer to the exhibit.

You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
Refer to the exhibit.
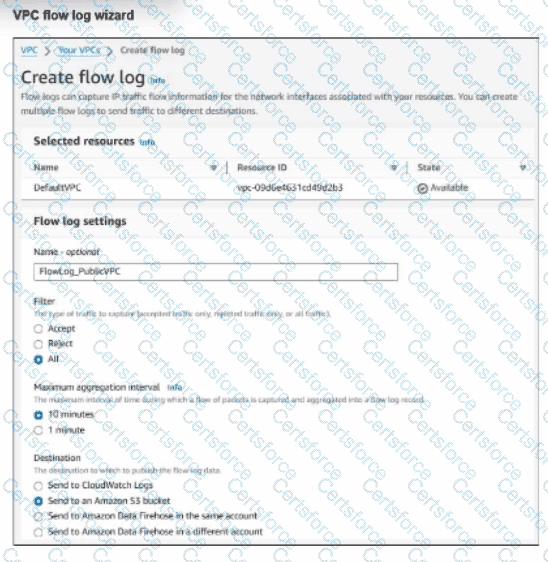
An experienced AWS administrator is creating a new virtual public cloud (VPC) flow log with the settings shown in the exhibit.
What is the purpose of this configuration?
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
What would be the impact of confirming to delete all the resources in Terraform?

Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
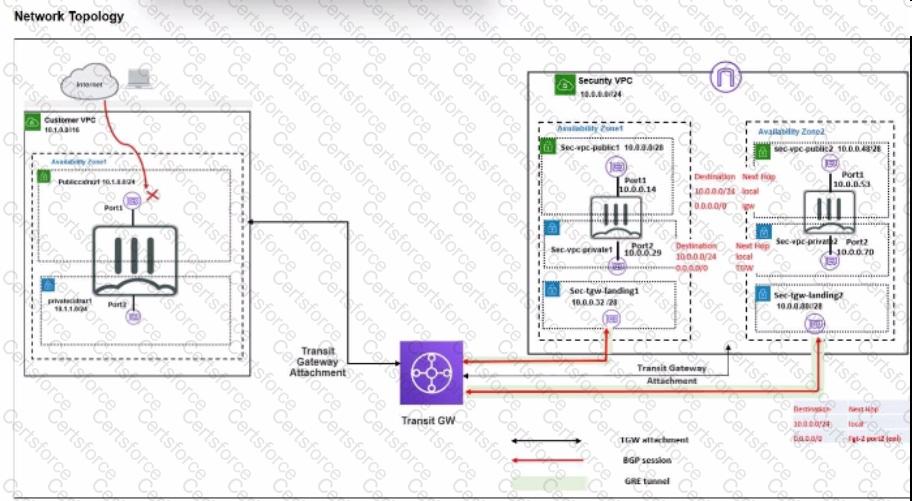
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)