Which running mode takes the most time to perform machine learning tasks?
Refer to the exhibit.
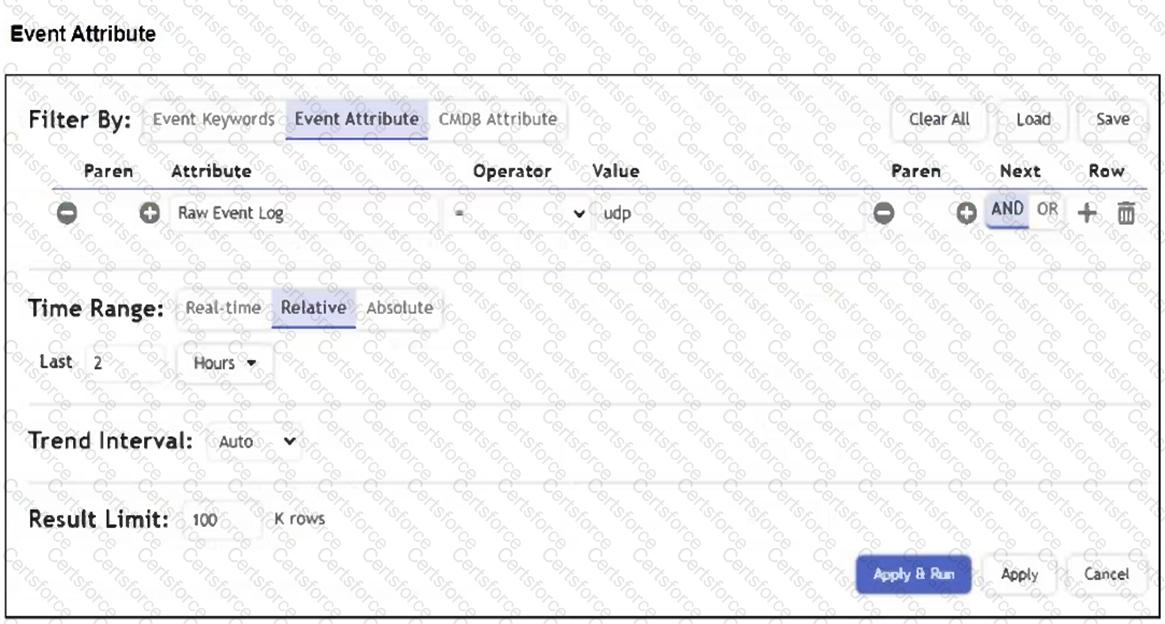
A FortiSIEM device is receiving syslog events from a FortiGate firewall. The FortiSIEM analyst is trying to search the raw event logs for the last two hours that contain the keyword "udp". However, they are getting no results from the search, which they know should be available. Based on the filter shown in the exhibit, why are there no search results?
Refer to the exhibit.

Which value would you expect the FortiSIEM parser to use to populate the Application Name field?
How does FortiSIEM update the incident table if a performance rule triggers repeatedly?
Refer to the exhibit.
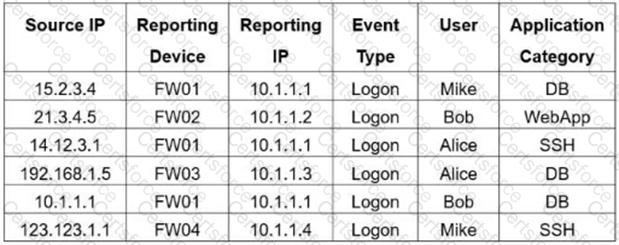
If you group the events by Reporting Device, Reporting IP, and Application Category, how many results will FortiSIEM display?
Refer to the exhibit.
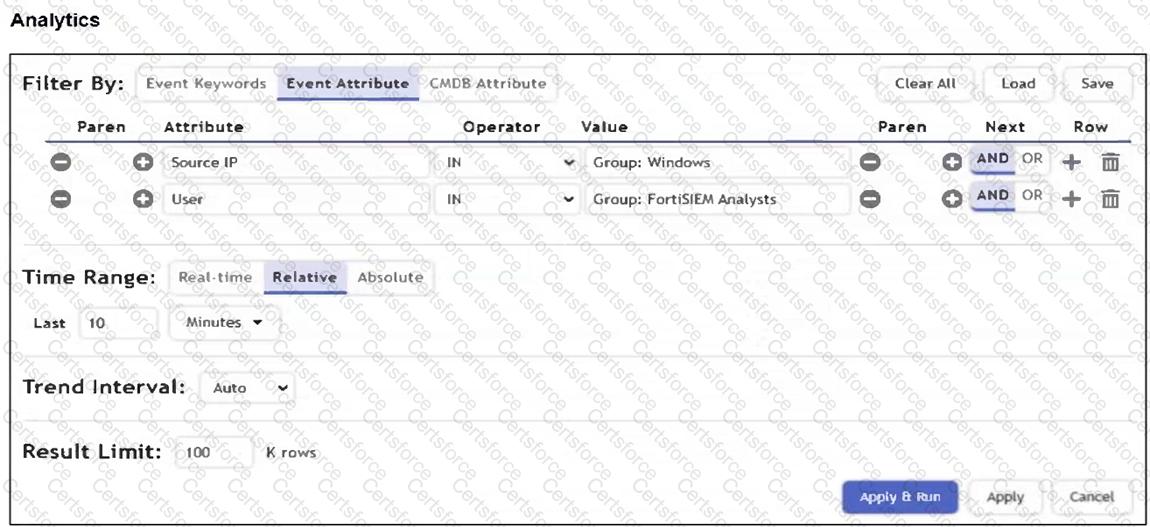
What is the Group: FortiSIEM Analysts value referring to?
Refer to the exhibit.
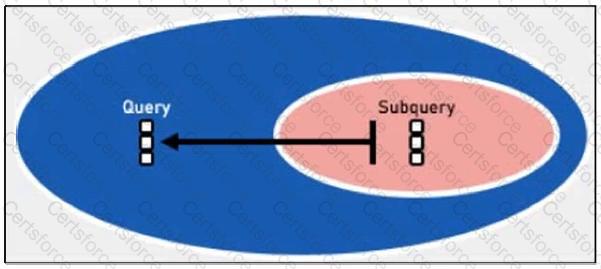
Which two lookup types can you reference as the subquery in a nested analytics query? (Choose two.)
Refer to the exhibit.
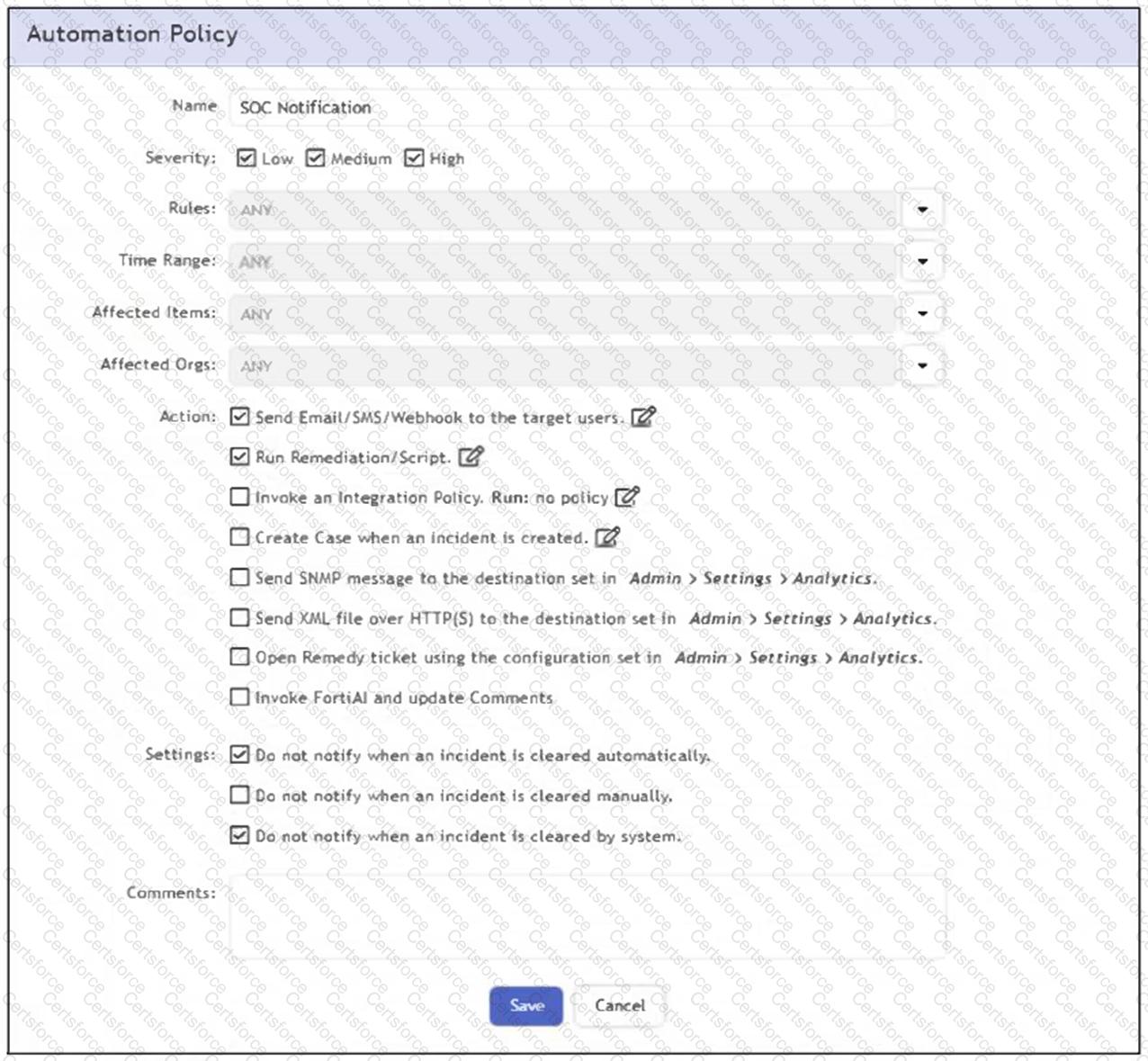
What happens when an analyst clears an incident generated by a rule containing the automation policy shown in the exhibit?
Refer to the exhibit.
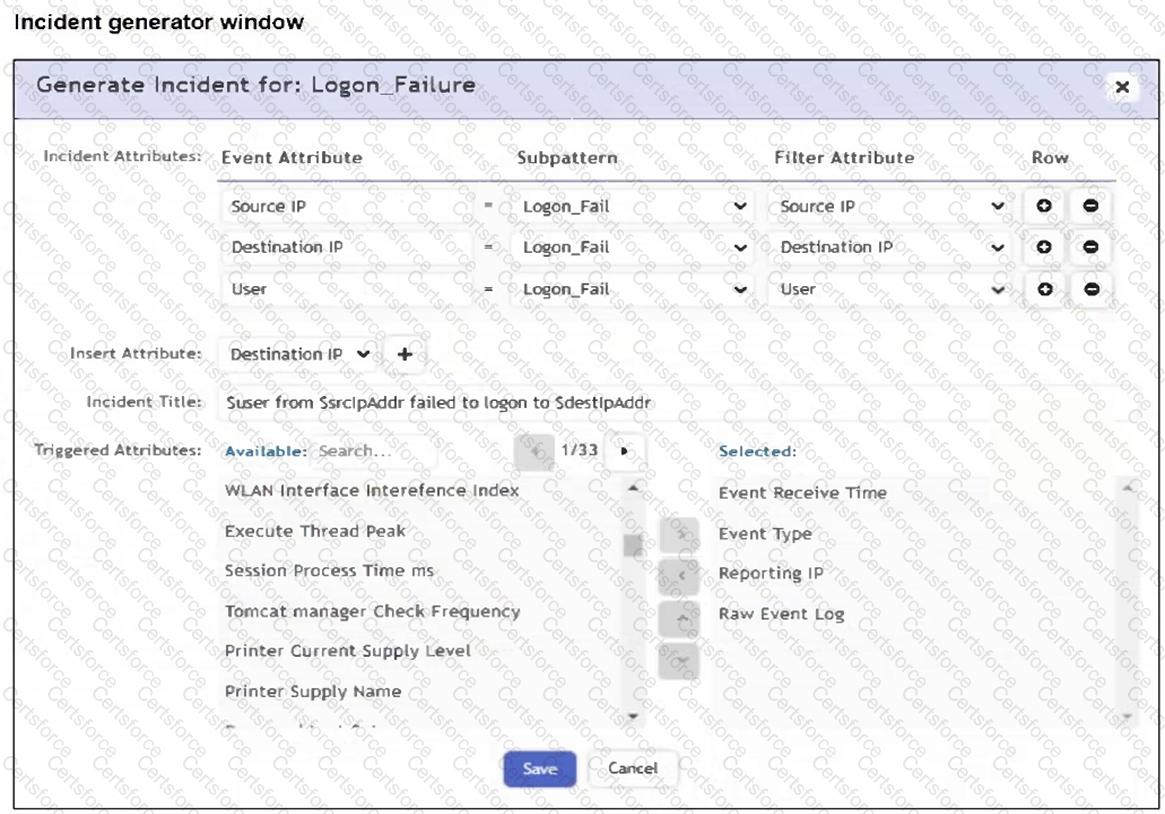
An analyst is trying to generate an incident with a title that includes the Source IP, Destination IP, User, and Destination Host Name. They are unable to add a Destination Host Name as an incident attribute.
What must be changed to allow the analyst to select Destination Host Name as an attribute?