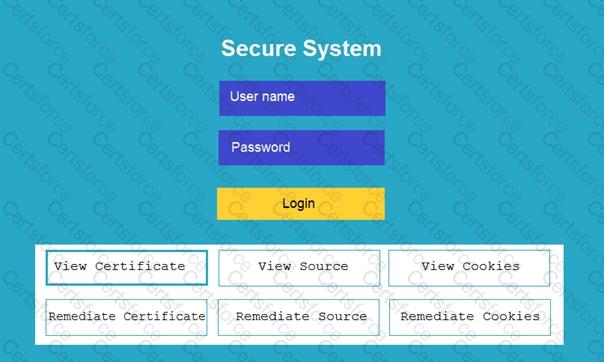
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
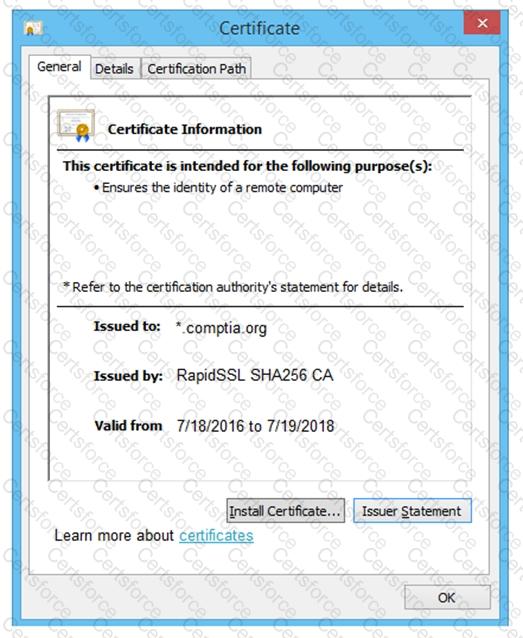
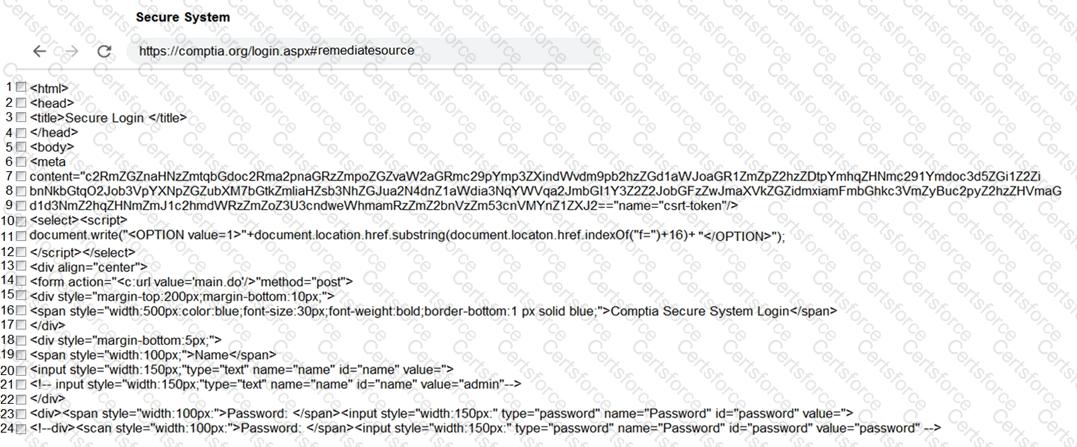
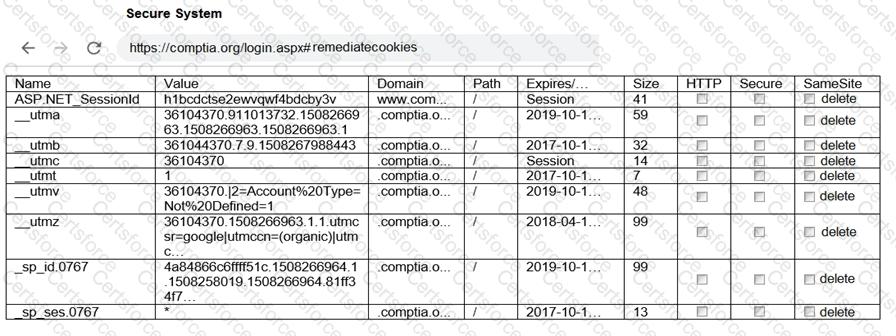
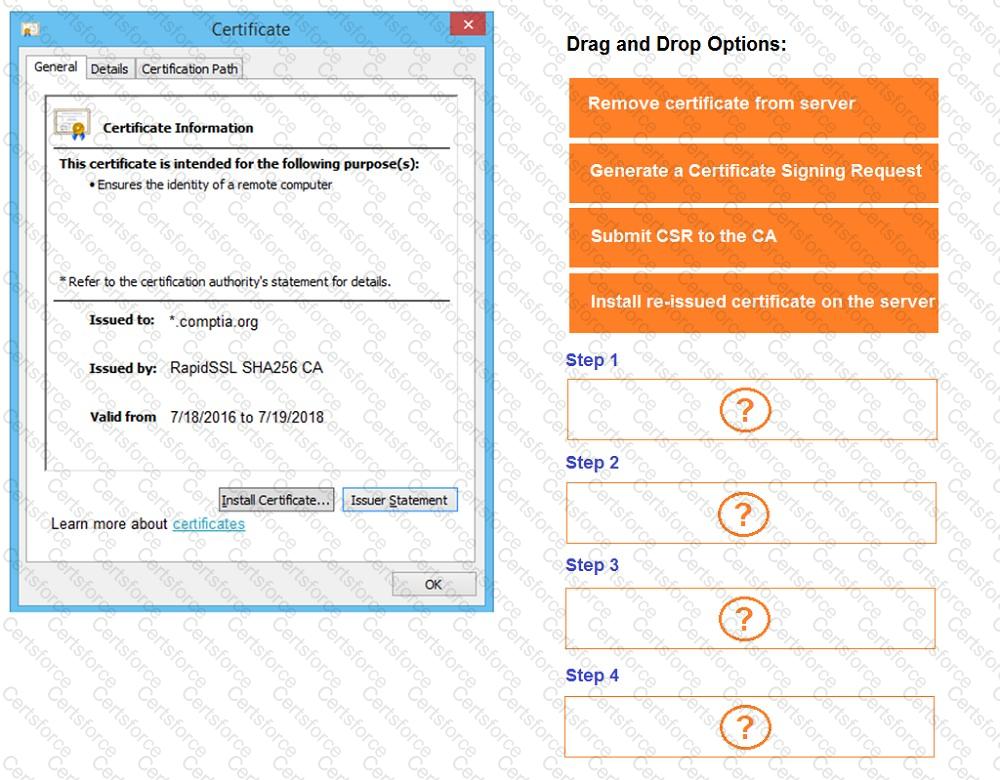
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Submit