A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
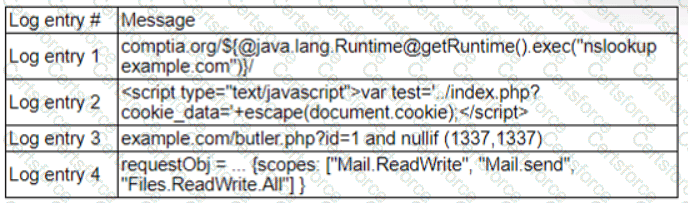
Which of the following log entries provides evidence of the attempted exploit?
Submit