An organization's finance system was recently attacked. A forensic analyst is reviewing the contents Of the compromised files for credit card data.
Which of the following commands should the analyst run to BEST determine whether financial data was lost?
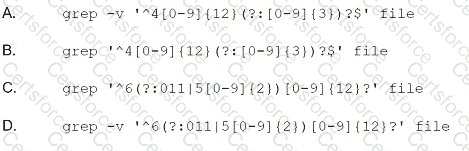
Submit