The Timebox to deliver the online reservation system through the Hoy Hall website has experienced a major issue. During Timebox C a test was completed to
simulate an attack on the financial element of the online reservation system, with the intention of finding security weaknesses. It was found that it was
potentially possible to gain access to the system, its functionality and data. Further work is therefore needed to meet the information security elements of a
customer financial transaction.
Answer the following question about the actions to be taken by each role.
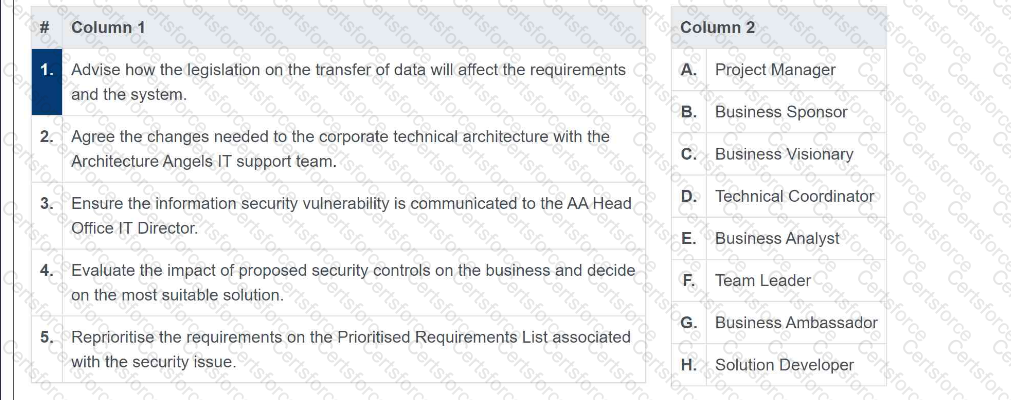
Column 1 describes a list of actions related to dealing with the security issue with the hotel reservation system. Column 2 lists the key roles. For each action in Column 1,
select from Column 2 the role that should carry out the action.
Each selection from Column 2 can be used once, more than once or not at all.
Column 1
Advise how the legislation on the transfer of data will affect the requirements
and the system.
Agree the changes needed to the corporate technical architecture with the
Architecture Angels IT support team.
Ensure the information security vulnerability is communicated to the AA Head
Office IT Director.
Evaluate the impact of proposed security controls on the business and decide
on the most suitable solution.
Reprioritise the requirements on the Prioritised Requirements List associated
with the security issue.
Column 2
Project Manager
Business Sponsor
Business Visionary
Technical Coordinator
Business Analyst
Team Leader
Business Ambassador
Solution Developer
Submit