Which of the following is TRUE about a Hash Search?
How do you rename fields while using transforming commands such as table, chart, and stats?
Which document provides information on best practices for writing Splunk-based hunting queries, predefined queries which may be customized to hunt for suspicious network connections, and predefined queries which may be customized to hunt for suspicious processes?
When exporting the results of the following event search, what data is saved in the exported file (assuming Verbose Mode)? event_simpleName=*Written | stats count by ComputerName
The Process Timeline Events Details table will populate the Parent Process ID and the Parent File columns when the cloudable Event data contains which event field?
What topics are presented in the Hunting and Investigation Guide?
Which field should you reference in order to find the system time of a *FileWritten event?
In the Powershell Hunt report, what does the "score" signify?
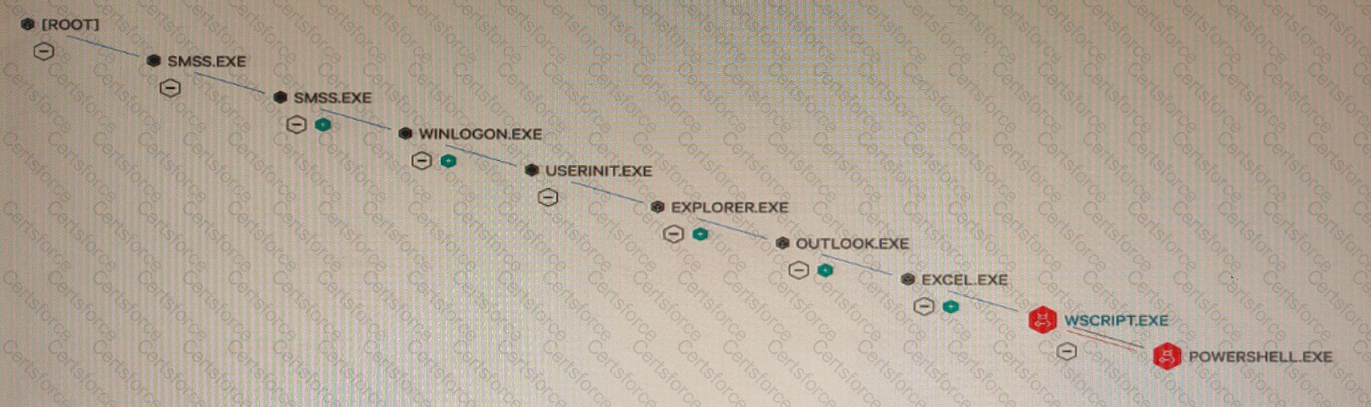
What type of attack would this process tree indicate?
What information is shown in Host Search?