You have allocated the correct number of buffers for your distance and speed on an extended distance link over dark fiber. However, you notice a latency issue being reported and the port is repeatedly starved for buffer credits.
What causes this to happen?
You want to provision an additional FCIP tunnel between your data centers. You have FCP acceleration features enabled on the tunnels.
What must you do?
A customer wants to connect an ISL between a Brocade DCX 8510 and a Brocade 5300 which are located 20 km apart at 8 Gbps through a DWDM.
Which two changes are required to the ports to enable error correction and communication between the devices? (Choose two.)
You have configured ports 0-2 on your Brocade 6520 to a distance of 50 km at 16 Gbps. As shown in the exhibit, port 2 was allocated more buffer credits than the other ports.
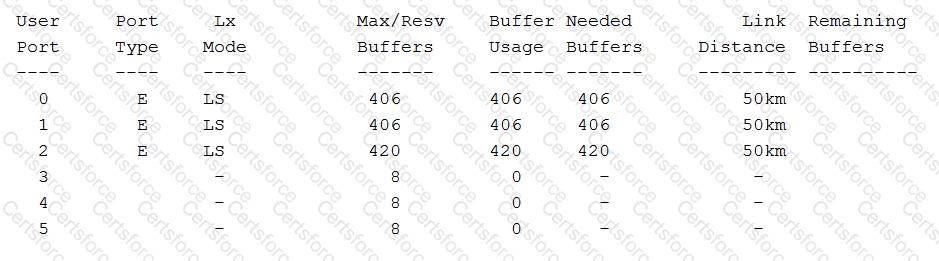
What is the reason for this happening?
Which feature is used when connecting a Brocade 6510 in Access Gateway mode to different fabrics while maintaining device-to-fabric consistency?
Which action is performed by an Access Gateway (AG) during the N_Port login process?
You must restrict which storage arrays can connect to your Gen 5 fabric.
Which security policy satisfies this requirement?