Spinning up a large number of temporary mining servers is likely part of what type of attack?
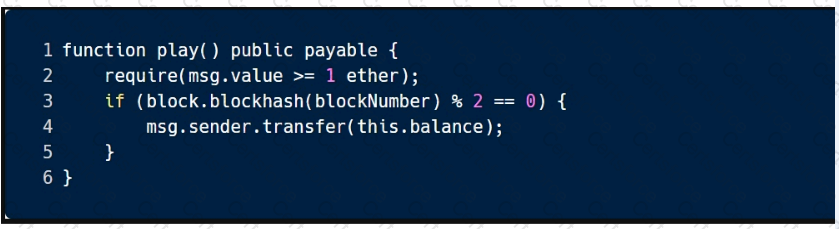
This sample code is vulnerable to which of the following attacks?
A network design where some nodes are prohibited from communicating directly with other nodes does not compromise the security of the blockchain.
Which of the following attacks were enabled by design decisions made by the blockchain's developers? Select all that apply
Stealth addresses are designed to do which of the following?
Which of the following is NOT an essential part of Confidential Transactions?
From a business perspective, which of me following is the major consideration regarding the use of smart contract technology?
Which smart contract vulnerabilities can be exploited by a malicious miner? Select all that apply
A major advantage of a stale channel is that it provides a permanent means of transferring value between two parties.
Which smart contract auditing strategy identities which variables in the function can be affected by the person running it?